Sidechain is a different kind of Cybersecurity Provider. We focus strictly on data security solutions to help you secure data, pass audits, and sleep better at night knowing your most sensitive assets are always monitored by experts 24x7.
We're not generalists: We are specialists that live and breathe encryption and key management.
Our implementations consistently pass GDPR, PCI-DSS, and HIPAA audits with documentation that regulators approve.
Your data security is continuously monitored by encryption specialists, proactively resolving issues and escalating alerts.
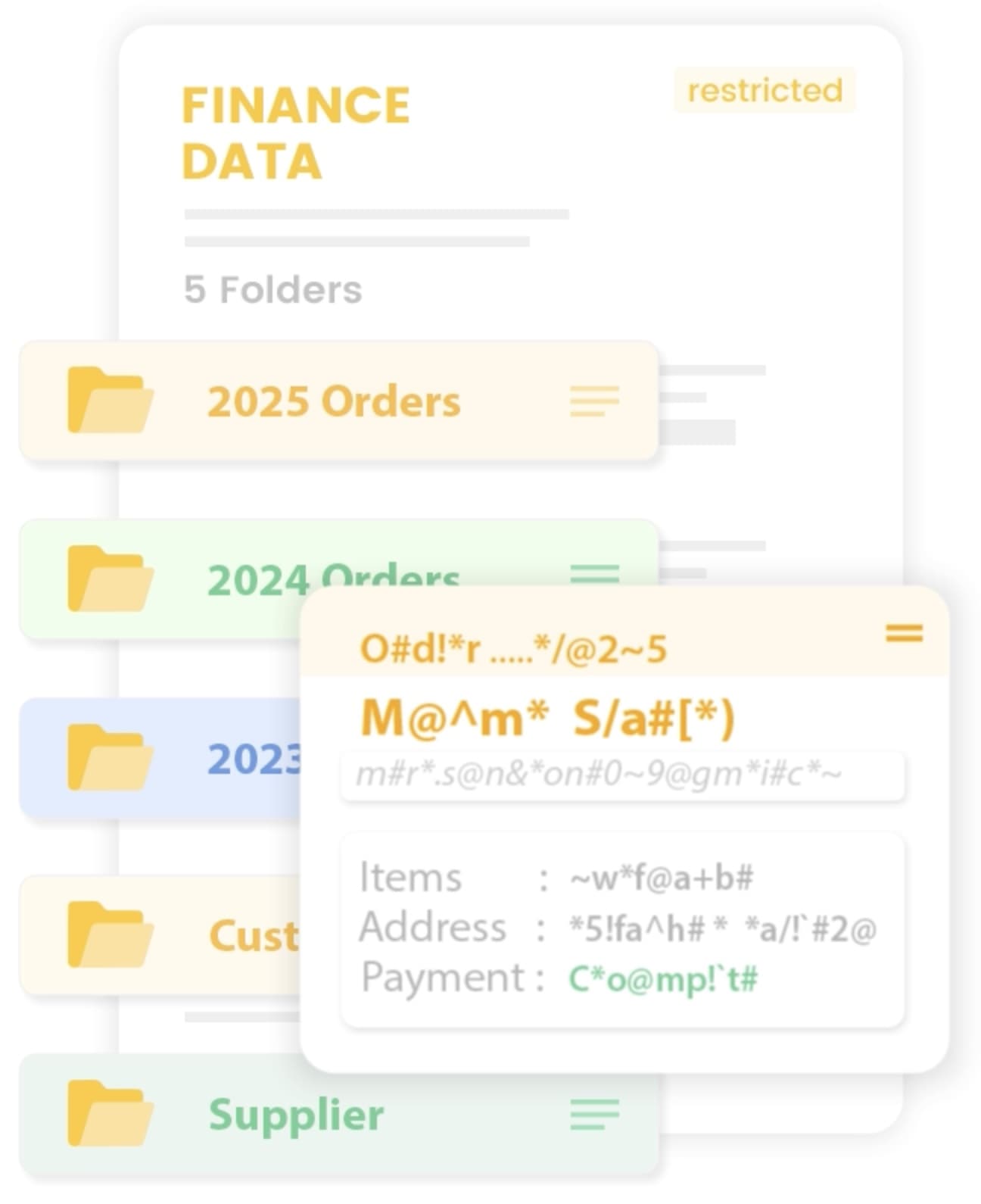
No matter what your data footprint looks like, our platform has you covered. Fully integrated encryption technologies, ironclad key management, and compliance reports at your fingertips.
Secure all your sensitive data sources and workloads in a unified platform, delivered as a service with nothing to deploy, nothing to manage, and no specialized skills required
Key security is often an afterthought, but with Sidechain, you get a fully-integrated, high security key management infrastructure (KMI) delivered from the cloud
Hardware Security Modules are a necessary, but cumbersome security add. Sidechain makes achieving FIPS 140-2 Level 3 easy with our data center-based HSM hosting service
We offer complete managed services for the following encryption and key management vendors. Our certified engineers ensure 100% operational stability, ensuring you get the most out of your investment in these solutions
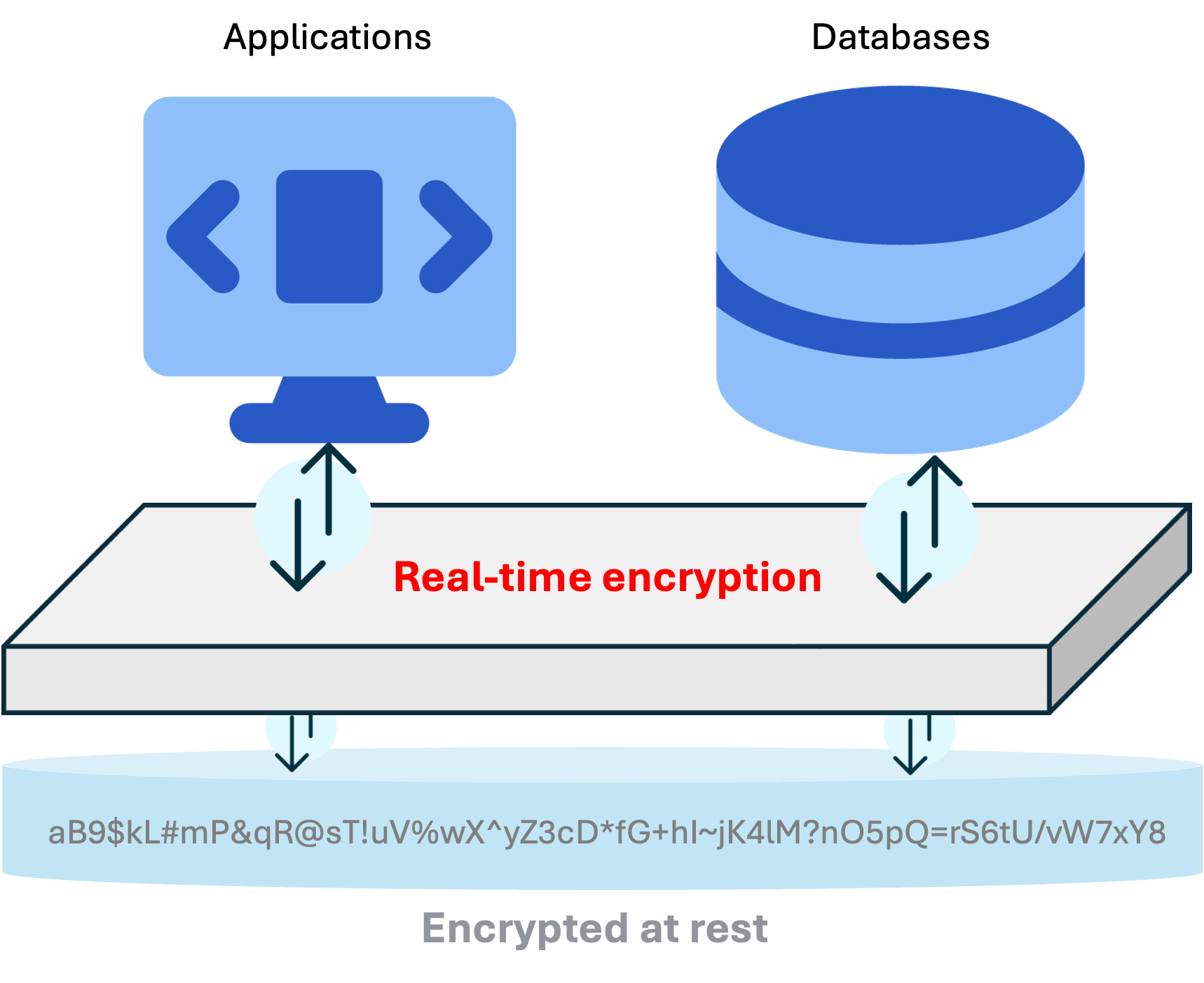
Zero changes required for applications and databases with undetectable performance impact. Enable encryption-at-rest in minutes, not days and weeks.
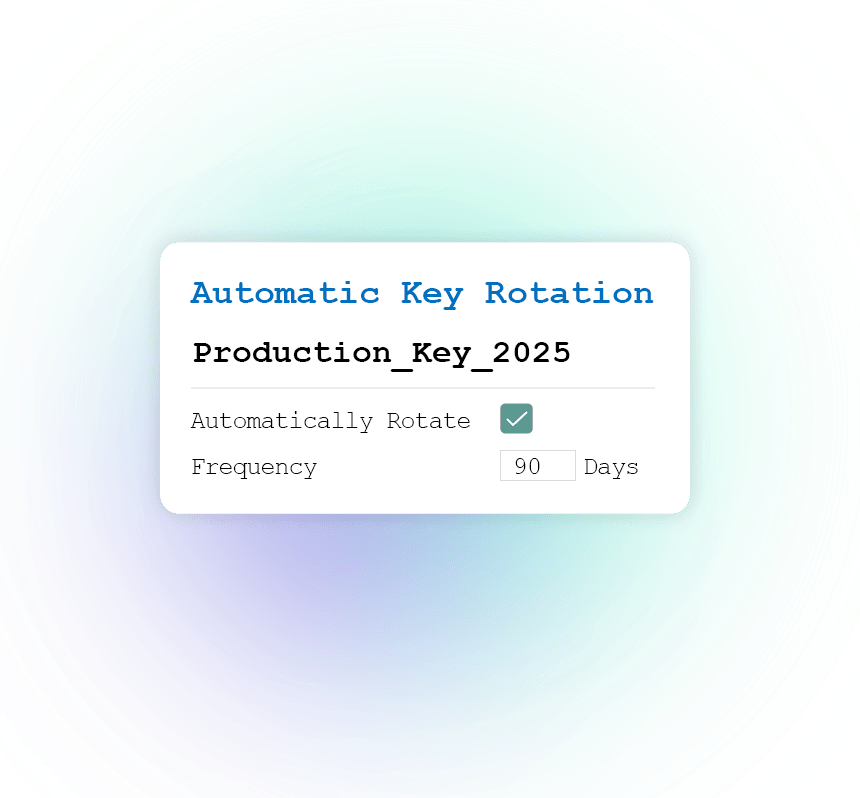
With automatic key rotation, you'll always stay compliant and maintain a strong security posture. Key rotation requires zero downtime, and doesn't interrupt workloads.
Target encryption to the data that requires it by fine-tuning policies and Guardpoints. Protect files, directories, volumes, Kubernetes workloads, and cloud assets.

You need bulletproof data protection. You don't need the operational overhead and complexity that usually comes with it.

"Of the countless things on my team's plate, managing encryption infrastructure isn't a priority for us. It's pure overhead, especially since it only touches a small portion of our overall environment. But we still need it done right for compliance.
I'm happy to let Sidechain handle all of that so my engineers can focus on projects that actually move our business forward. They know encryption better than we ever will, and frankly, we don't want to become experts in something that's not our core competency."
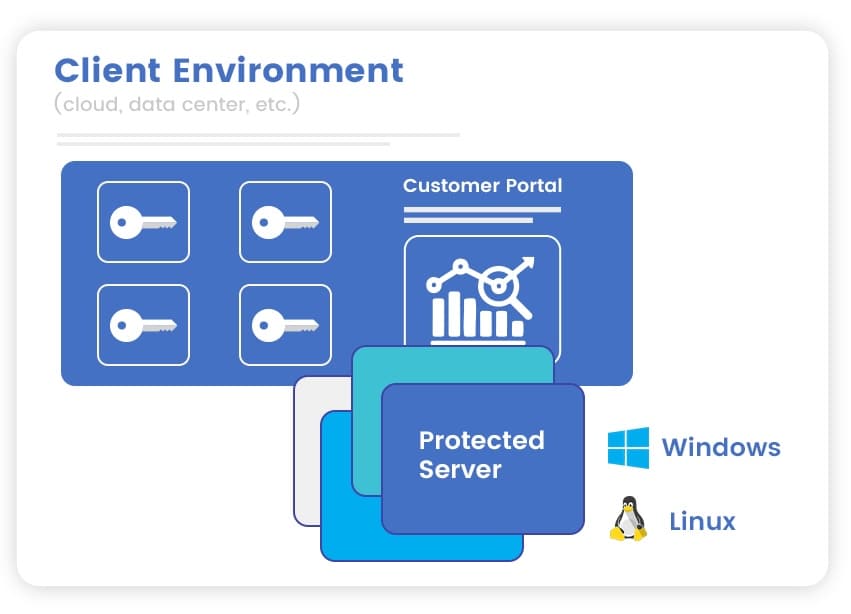
Sidechain runs the complicated key management infrastructure (KMI) in our high-availability cloud. Each of your systems that needs encryption has a small encryption agent that registers to the KMI. Once registered, you're ready to secure data!
Data-at-rest encryption for Windows and Linux. Quickly encrypt files, folders, directories, and volumes.
Supports databases, file servers, unstructured data, and more.
Immediate deployment at the lowest cost point, rock-solid data security, guaranteed to pass audits and security questionnaires.
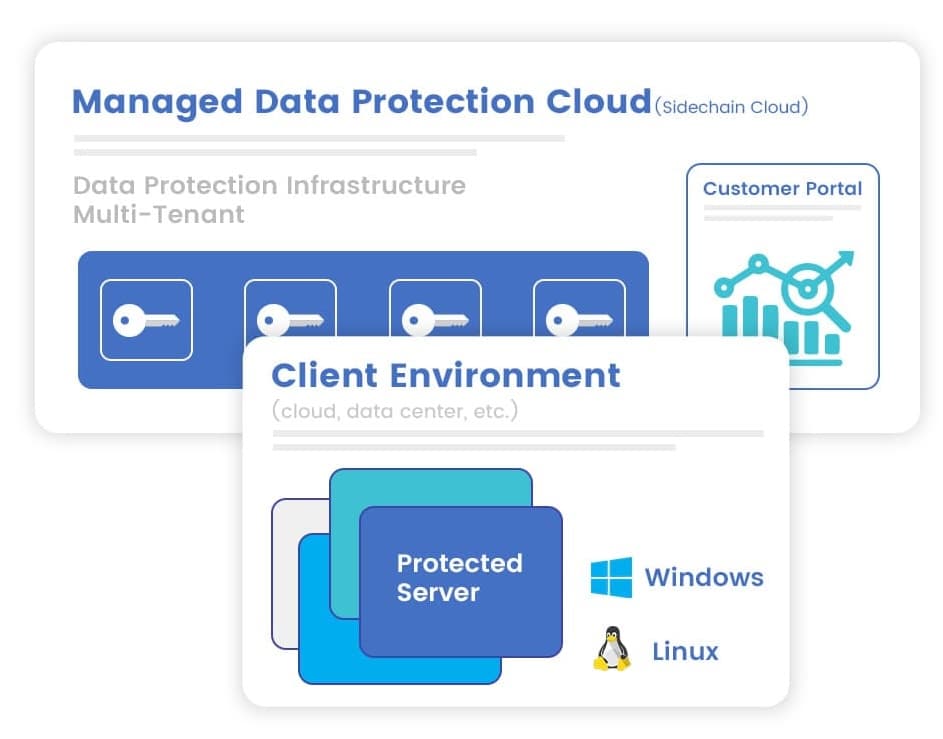
We offer two additional tenant configurations for enterprise customers:
Both Single-tenant and On-premises configurations support additional Hardware Security Module (HSM) integration for strong key security and FIP 140-2 Level 3 certification.
Enterprise subscriptions qualify for Named Engineer Support. Your dedicated account engineer knows you, your team, your deployment, and is first-line support for any issues you have.
A lot goes into managing a resilient, error-free key and encryption platform.
Delivering a rock-solid data protection service includes strong encryption know-how and the ability to deliver it as a service with the uptime and stability you expect.
Whether you are looking for advice, confidential feedback, or just want to vent, we're here to listen. Let's chat!
