Get the highest level of cryptographic protection through managed Hardware Security Modules hosted in ultra-secure data centers. Our HSM-as-a-Service rapidly delivers FIPS 140-2 Level 3 compliance. No procurement delays, no specialized staffing, no operational complexity - just tamper-resistant key protection that meets the most stringent security requirements.
Achieve FIPS 140-2 Level integration and compliance evidence in as little one week
Zero hardware procurement or data center requirements
Geo-redundant and built to your security specifications
While many vendors offer "cloud HSM" services, Sidechain is the only provider that builds hosted HSM management to your specifications, in data centers you can audit.
Eliminate the complexity and risk of managing HSM's. Our certified engineers setup, and maintain HSM's for your needs.
Why buy hardware? Sidechain acquires, racks, stacks, and amortizes the cost into an easy, predictable monthly subscription.
We build our HSM hosting to your security specifications, provide a complete audit of our data centers.
HSM's are necessary method for certifying against FIPS 140-2 Level 3, yet deploying hardware in a virtualized and cloud infrastructure is prohibitive. Cloud-based HSM's integrate seamlessly with no hardware to deploy.


Integrating HSM's into your applications can be the most difficult part. Our certified engineers have been through HSM integrations and will take care of the heavy lifting.
Unlike vendor cloud-HSM services which are operated in a black box, you have full control over the security posture of your HSM infrastructure. We offer single-tenant, segmented hardware cages, and monitoring alerts sent right to your inbox.

"Of the countless things on my team's plate, managing encryption infrastructure isn't a priority for us. It's pure overhead, especially since it only touches a small portion of our overall environment. But we still need it done right for compliance.
I'm happy to let Sidechain handle all of that so my engineers can focus on projects that actually move our business forward. They know encryption better than we ever will, and frankly, we don't want to become experts in something that's not our core competency."
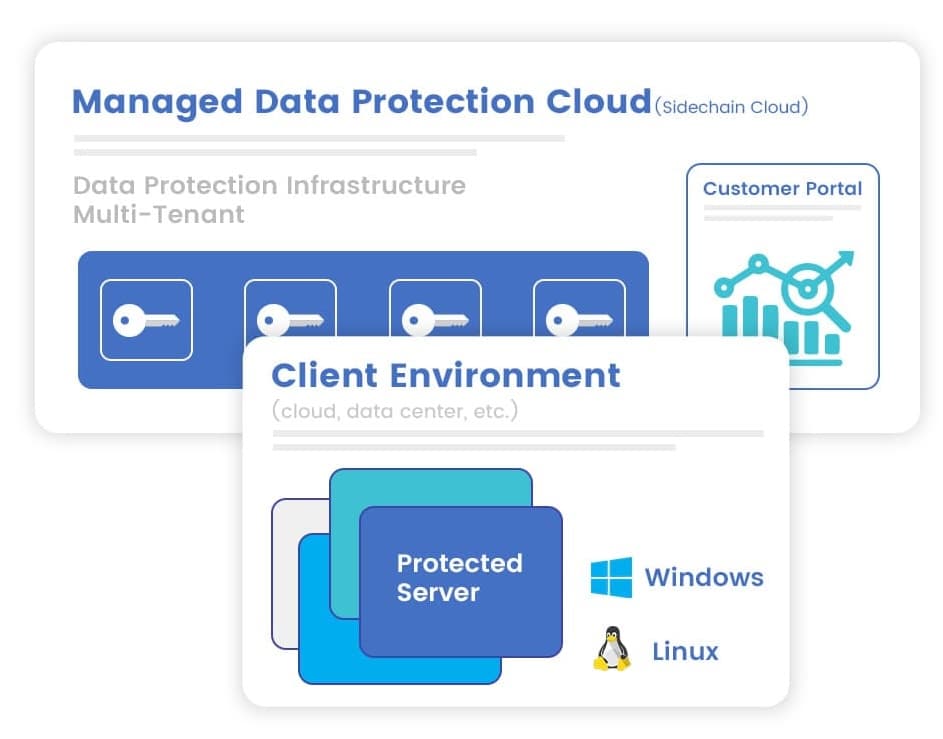
Sidechain operates 5 data center locations throughout in the US and Europe. We work with you to understand your security requirements and build a hosted, managed HSM solution to-spec. We fulfill all infrastructure and management requirements and offer integration services.
We support the following purchase and deployment options:
Immediate deployment at the lowest cost point, rock-solid data security, guaranteed to pass audits and security questionnaires.
A lot goes into managing a resilient, error-free key and encryption platform.
Delivering a rock-solid data protection service includes strong encryption know-how and the ability to deliver it as a service with the uptime and stability you expect.
Whether you are looking for advice, confidential feedback, or just want to vent, we're here to listen. Let's chat!
